Cloud Security and Defense insights: Defending Against the GUI-vil Threat Actor
Cloud Security & Defense insights: Defending Against the GUI-vil Threat Actor
In this guide, we will go through GUI-vil threat actor attack patterns together and define some detection rules to discover the attack using Falco with the CloudTrail plugin installed, along with other tools.
Who is GUI-vil?
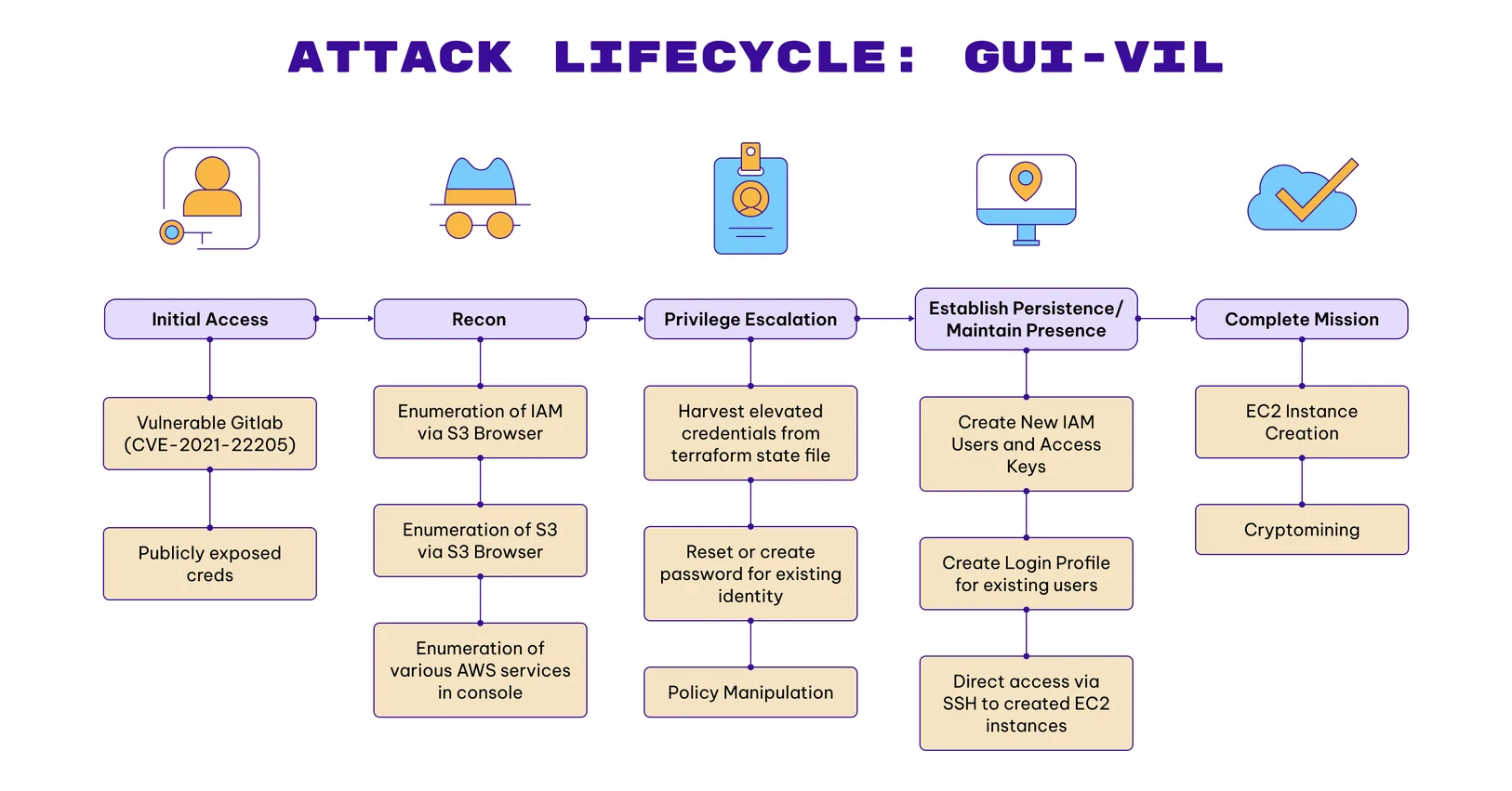
GUI-vil a financially motivated adversary uncovered by Permiso’s p0 Labs after 18 months of tracking. Originating from Indonesia, this group stands out by favoring graphical interfaces over traditional command-line tooling—hence the name “GUI-vil.”
GUI-vil exploits cloud infrastructure, specifically AWS, to spin up EC2 instances for unauthorized crypto mining—leaving victims to foot massive cloud bills. Unlike more advanced attackers using automated scripts and CLI tools, GUI-vil takes a more “manual” approach, often interacting via:
- The AWS Management Console in a browser
- Outdated tools like S3 Browser v9.5.5 (from 2021)
How They Get In
GUI-vil isn’t hacking in via zero-days—they’re opportunists. Here’s how they typically breach environments:
- Hunting for Exposed AWS Keys on GitHub, Pastebin, etc.
- Scanning for vulnerable GitLab instances
- Exploiting known CVEs, like CVE-2021-22205
- Abusing publicly available credentials
Blending In
Once inside, GUI-vil tries to fly under the radar by:
- Creating usernames that mimic legitimate naming patterns
- Adding login profiles to existing IAM users (where none existed before)
- Using legit-looking activity to avoid raising alarms
Staying Resilient
GUI-vil doesn’t just break in—they try to stay in. When detected, they actively pivot and re-establish access, making them difficult to root out without thorough remediation.
Their activities have been traced back to Indonesian ISPs, including:
- PT. Telekomunikasi Selula
- PT Telekomunikasi Indonesia
Why This Matters
For many orgs, the cost of exploited EC2 usage far exceeds any gains the attacker makes from mining crypto. This makes GUI-vil not just a threat to data—but also to cloud cost control and operational stability.
Defense Tips
To protect your environment from actors like GUI-vil:
- Continuously monitor for exposed credentials
- Audit IAM activity for suspicious user creation or profile changes
- Use anomaly detection for console-based access patterns
- Enforce least privilege access and MFA across all accounts
- Track usage of outdated third-party tools like S3 Browser
Monitor for Exposed Credentials
Tools:
- TruffleHog
- Gitleaks
You can integrate these tools directly into your CI pipelines (e.g., GitHub Actions or GitLab CI) to automatically scan for exposed secrets in every commit or pull request. This helps catch leaked credentials before they reach your cloud environment.
Gitleaks with Gitlab example
- Add it as a job in your .gitlab-ci.yml to scan each commit or merge request.
- Supports custom rules and baseline files to reduce noise.
Example GitLab CI config:
gitleaks_scan:
image: zricethezav/gitleaks:latest
script:
- gitleaks detect --source=. --verbose --redactAudit IAM Activity for Anomalies (CloudTrail Events)
Requirement: Falco must be set up with the CloudTrail plugin enabled.
- Detect IAM User Creation
- rule: CloudTrail IAM User Created
desc: Detect creation of a new IAM user via CloudTrail
condition: evt.name = "CreateUser"
output: "IAM User Created: user=%user.name awsRegion=%aws.region from=%aws.sourceIP"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, iam]- Detect IAM Login Profile Creation (used by GUI-vil for console access)
- rule: CloudTrail Login Profile Created
desc: Detect creation of a new IAM Login Profile
condition: evt.name = "CreateLoginProfile"
output: "Login Profile Created: user=%user.name from=%aws.sourceIP"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, persistence]Detect S3 Browser via User-Agent (CloudTrail)
Requirement: Falco must be set up with the CloudTrail plugin enabled.
- rule: CloudTrail Suspicious UserAgent - S3 Browser
desc: Detect access via known suspicious S3 Browser user-agent
condition: evt.useragent contains "S3Browser"
output: "S3 Browser access detected: userAgent=%evt.useragent account=%cloud.account"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, reconnaissance]📝 Tip: You can expand this rule with more suspicious user agents or look for outdated tool versions.
Detect Crypto Mining Behavior (CloudTrail)
Requirement: Falco must be set up with the CloudTrail plugin enabled.
- Multiple EC2 Instances Created
Falco doesn’t do time-based aggregation natively, but you can alert on any RunInstances event:
- rule: CloudTrail EC2 RunInstances
desc: Detect EC2 instance creation (monitor frequency via external alerting tools)
condition: evt.name = "RunInstances"
output: "EC2 Instance Launched: user=%user.name from=%aws.sourceIP"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, ec2]Use CloudWatch or SIEM to alert on burst patterns (e.g., >5 EC2s in 1 min).
Suspicious IAM User Naming Patterns (GUI-vil: new-user-*, sec_audit)
Requirement: Falco must be set up with the CloudTrail plugin enabled.
- rule: CloudTrail Suspicious IAM Username
desc: Detect suspicious IAM user naming convention
condition: evt.name = "CreateUser" and (user.name startswith "new-user-" or user.name = "sec_audit")
output: "Suspicious IAM username created: %user.name from=%aws.sourceIP"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, iam, evasion]Detect EC2 Key Pair Creation
Requirement: Falco must be set up with the CloudTrail plugin enabled.
- EC2 Key Pair Created
- rule: CloudTrail EC2 KeyPair Created
desc: Detect creation of an EC2 SSH key pair
condition: evt.name = "CreateKeyPair"
output: "EC2 KeyPair created: user=%user.name from=%aws.sourceIP"
priority: WARNING
source: cloudtrail
tags: [cloud, aws, persistence]Summary (All Falco CloudTrail-Based Rules)
| Detection | CloudTrail Event | Falco Rule Included |
|---|---|---|
| IAM User Created | CreateUser |
* |
| Login Profile Added | CreateLoginProfile |
* |
| Suspicious User Agent | userAgent = S3Browser |
* |
| EC2 Instances Created | RunInstances |
* |
| Key Pair Creation | CreateKeyPair |
* |
| Suspicious IAM Username Pattern | CreateUser + pattern |
* |
Thank you for reading, I hope you enjoyed it, see you in the next post.
Please subscribe to my twitter, to be notified when the next tutorial is published.
